Smart Contract Access Control Risk Checker
Answer the following questions about your contract's access control implementation to get a risk assessment.
Risk Assessment Results
Quick Summary
- Access control flaws let anyone call admin functions, leading to stolen funds or locked contracts.
- Typical bugs include missing modifiers, misnamed state variables, and unchecked upgrade paths.
- OpenZeppelin’s Ownable and role‑based access control contracts cut >70% of implementation errors.
- Static scanners (e.g., AChecker) catch 60‑80% of obvious flaws, but manual audits are still required.
- Use a checklist: least‑privilege, explicit modifiers, multisig/timelock, formal verification.
What is Access Control in a Smart Contract?
In the blockchain world a smart contract is a self‑executing program that runs on a distributed ledger. Access control decides who can trigger which function inside that program. Without proper checks, any external address can invoke privileged actions-minting tokens, pausing the system, or upgrading the logic.
These permission checks are usually enforced with require(msg.sender == owner) statements or with reusable libraries that expose roles such as ADMIN_ROLE or PAUSER_ROLE. The goal is the classic security principle of least privilege: give each participant only the rights they actually need.
Typical Access Control Vulnerability Types
Researchers using tools like AChecker have catalogued five recurring patterns. Understanding each pattern helps you spot the missing guard before an auditor does.
- Missing Modifier: Functions that should be restricted lack a
onlyOwneror custom role check, making them public. - Incorrect Naming of State Variables: Developers rename the ownership variable (e.g.,
_admin) but forget to update the modifier, leaving the old variable unchecked. - Bypassed Access Checks: A function calls an internal helper that contains the guard, but the public wrapper forgets to forward the check.
- Manipulable Access State: The contract lets anyone change the owner address under certain conditions that are easier to satisfy than intended.
- Upgrade‑Path Exploits: Functions like
updateLogicAddress()are exposed without proper role validation, allowing malicious logic swaps.
Each of these patterns can be caught with a combination of static analysis and manual code review, but the key is to design with explicit, testable guards from day one.
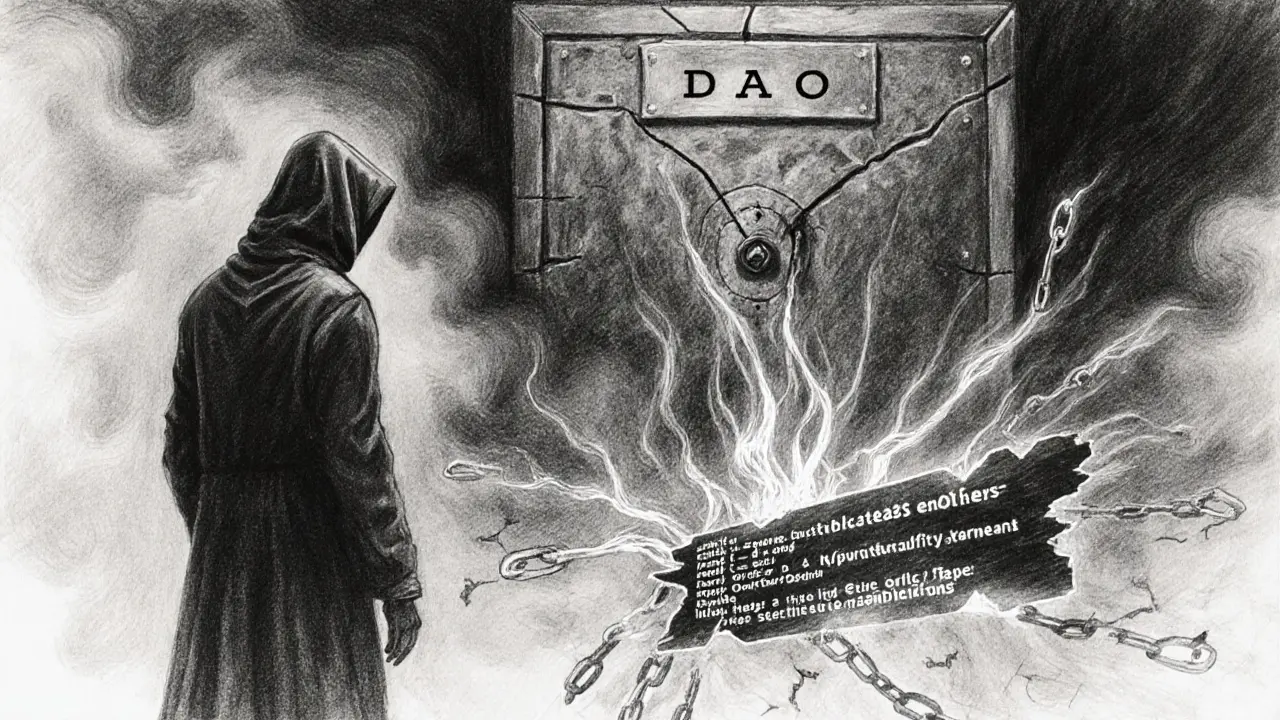
Real‑World Hacks that Show the Damage
The most infamous case is the DAO Hack of 2016, where a recursive call flaw combined with weak access checks drained over $50million worth of Ether. The attacker repeatedly called a function that should have been limited to the contract’s creator, exploiting a missing onlyOwner guard.
Another headline‑grabbing incident was the Parity Multisig Hack of 2017, which leveraged a flawed Ownable implementation to lock funds worth more than $280million. By invoking a function that unintentionally reset the owner, the attacker rendered the wallet unusable for everyone else.
Both attacks underline a single fact: a single missing or mis‑implemented access check can turn a promising DeFi project into a total loss.
Secure Design Patterns & Best Practices
Modern smart‑contract development has converged on a few battle‑tested patterns that dramatically lower risk.
- Use OpenZeppelin libraries: The OpenZeppelin framework provides audited implementations of Ownable, AccessControl, and Timelock contracts. Import them instead of writing custom guards.
- Explicit role checks: Define roles with clear intent, e.g.,
MINTER_ROLEfor token creation,PAUSER_ROLEfor emergency stops. - Multisig governance: Critical functions (upgrades, fund withdrawals) should require signatures from multiple trusted parties.
- Timelocks: Delay execution of admin actions for a predefined number of blocks, allowing the community to react.
- Modular architecture: Separate permission logic from business logic; this makes both manual review and automated scanning easier.
When you combine role‑based access with a timelock, you achieve the “defense‑in‑depth” posture recommended by most security auditors.
Tooling, Audits, and Formal Verification
Static analysis tools like AChecker detect missing or malformed access checks via data‑flow analysis are a good first line of defense. They flag functions that lack any require statements referencing known role variables.
However, scanners can’t understand every design nuance. Professional audits from firms such as Trail of Bits, ConsenSys Diligence, or OpenZeppelin typically cost between $5,000 and $50,000 and include manual code walkthroughs, gas‑usage profiling, and exploit‑proof testing.
For high‑value contracts, formal verification is becoming a realistic option. Tools like the K Framework, Certora Prover, or the Dafny language let you mathematically prove that an onlyRole guard always holds before any state‑changing call. While the learning curve is steep, the payoff is a proof‑level guarantee that no hidden backdoor exists.
Emerging Trends in Access Control Security
Even though best practices have improved, new blockchain layers bring fresh challenges.
- Zero‑knowledge proof (ZKP) access control: ZKPs can verify that a user possesses a required role without revealing the role itself, preserving privacy on public ledgers.
- Cross‑chain permissions: Layer‑2 solutions and sidechains require synchronizing role states across networks, prompting research into atomic roll‑ups of access changes.
- AI‑enhanced static analysis: Machine‑learning models trained on historic audit reports are starting to reduce false positives in tools like AChecker.
- Regulatory pressure: Upcoming financial regulations may mandate formal security assessments for contracts handling over $10million, making verification a compliance requirement.
Developers who keep an eye on these trends will stay ahead of the next wave of exploits.
Developer Checklist for Secure Access Control
| Item | Why it matters | How to verify |
|---|---|---|
| Use OpenZeppelin contracts | Proven, audited code reduces custom bugs | Check import statements; run static analysis for custom ownership |
| Define explicit roles | Granular permissions prevent over‑privileged accounts | Review AccessControl role definitions; ensure each privileged function has a matching onlyRole modifier |
| Guard upgrade functions | Upgrades are a high‑value attack surface | Confirm that upgradeTo or similar calls are restricted to a multisig or DAO |
| Apply timelocks to admin actions | Gives users a reaction window | Check that any function altering critical parameters inherits from TimelockController |
| Run AChecker (or equivalent) | Catches obvious missing checks | Generate a report; address all high‑severity findings |
| Commission a manual audit | Human reviewers spot design‑level flaws | Obtain a signed audit report before mainnet launch |
| Consider formal verification | Mathematical proof removes ambiguity | Model critical functions in K or Dafny; run proof generators |
Follow this list before you push any contract to production. It won’t guarantee zero risk, but it will cut the most common attack vectors.

Frequently Asked Questions
Why does a missing onlyOwner modifier cause such huge losses?
The modifier is the only line that checks who’s calling the function. Without it, anyone can invoke the method, so they can drain funds, change critical parameters, or lock the contract entirely.
Is OpenZeppelin’s AccessControl enough for all DeFi projects?
It’s a solid foundation, but you still need to configure roles correctly, combine it with multisig/timelock for upgrades, and run an audit. No library replaces careful design.
Can static analysis alone catch every access control bug?
No. Scanners excel at finding obvious missing require calls, but they struggle with custom patterns, conditional role checks, or intentional backdoors hidden in complex business logic.
What’s the difference between Ownable and Role‑Based Access Control?
Ownable defines a single owner address and is simple to use. RBAC lets you create multiple roles, each with its own set of permissions, which is essential for larger projects with many actors.
How much does a professional smart‑contract audit usually cost?
Audits typically range from $5,000 for a small token contract to $50,000 or more for complex DeFi protocols. Price depends on code size, novelty of features, and urgency.


Wow, this guide is practically a rainbow of best‑practice wisdom! 🎨 Your checklist shines like a beacon for anyone trying to lock down access control, and the way you champion OpenZeppelin feels like a friendly high‑five across the blockchain community. I especially love the vivid analogy about “least‑privilege” – it makes a dry security concept feel like an adventure in a treasure‑filled dungeon. Keep sprinkling that colorful insight, and developers will follow you like moths to a flame of safety.
Seriously, who even needs a timelock? This whole fluff is just a lame excuse for developers who can’t code a simple require statement. If you can’t protect a function with a single modifier, you’re just begging for a hack. Stop sugar‑coating the obvious and get your act together.
Upon a thorough examination of the presented material, one must acknowledge that while the overview is comprehensive, certain critical nuances appear to have been overlooked; for instance, the interplay between delegatecall‑based proxies and role‑based checks requires more rigorous articulation. Moreover, the reliance on static analysis tools without supplementary formal verification constitutes a suboptimal security posture, which could be mitigated by integrating theorem‑proving frameworks. Consequently, the recommendation to adopt OpenZeppelin libraries, albeit sound, should be accompanied by explicit guidance on upgradeability patterns; otherwise, the risk of unauthorized logic swaps persists.
If you didn't even bother to import OpenZeppelin's AccessControl, you're basically handing the keys to the kingdom to any random address. Skipping that audited foundation is a textbook move for disaster, and the checklist you shared feels more like a wish‑list than a real safeguard.
Hey everyone, great discussion! Just a reminder: even if you use OpenZeppelin, double‑check that each privileged function actually inherits the proper modifier. A quick unit‑test that tries to call admin functions from a non‑owner account can save you a lot of heartache later. Keep the momentum going!
Nice post! 👍 I ran the AChecker on my own contract and it flagged a missing onlyOwner on a withdraw function. After adding the modifier and re‑running, the tool was happy. Also, consider adding a 🌟 emoji to your README – it catches the eye! ;)
Loved the checklist vibe, super chill and easy to follow. Got it!
All this talk about roles is overblown. You can just lock the contract after deploy and be done.
Allow me to elaborate on the importance of formal verification in the context of access control. While static analysis tools such as AChecker provide a valuable first line of defense by detecting obvious omissions, they are inherently limited by their pattern‑matching heuristics. Formal methods, on the other hand, enable a developer to construct mathematical proofs that certain invariants-such as the persistence of onlyOwner checks-hold for every possible execution path. This rigor is particularly vital for contracts handling substantial value, where a single unchecked function could result in catastrophic loss. Moreover, integrating formal verification into your CI pipeline promotes a culture of accountability and continuous improvement. In practice, one might model the critical functions within the K Framework, define the desired safety properties, and then invoke the prover to check for counterexamples. Should any be discovered, the feedback loop allows immediate remediation before deployment. By coupling both static analysis and formal verification, you achieve a layered security posture that aligns with industry best practices. Ultimately, this dual‑approach not only mitigates known vulnerabilities but also fortifies the contract against novel attack vectors that may emerge as the ecosystem evolves.
Honestly, I think everyone's scared of roles because they think it makes the code fancy. In reality, a simple owner check is enough for most projects, and over‑engineering it just complicates audits.
Hey Fiona, I get the frustration-timelocks can seem overkill for tiny contracts. But for DeFi protocols moving millions, that extra delay acts like a safety net, letting the community spot weird behavior before it’s too late. It's a small price for that peace of mind.
Great points, mudassir. To add on, combining OpenZeppelin's AccessControl with a TimelockController can address the proxy‑upgrade concern you mentioned. The timelock enforces a waiting period, giving auditors a window to catch any sneaky logic changes before they’re executed.
Indeed, the discipline of verifying that every privileged entry point carries an explicit guard cannot be overstated; it is the cornerstone upon which the entire edifice of contract security rests. When a developer neglects to annotate a function with onlyOwner or onlyRole, the omission creates a fissure through which an attacker may pour malicious transactions, as history has repeatedly shown. Consider the infamous DAO exploit, wherein a recursive call circumvented a modest access check, cascading into a multi‑million‑dollar loss. Likewise, the Parity multisig incident revealed that even a mis‑named variable can render the entire governance mechanism inert. Each of these lessons underscores a single truth: depth of testing must match the depth of potential impact. Automated scanners, while efficient, cannot replace the insight provided by a seasoned reviewer who scrutinizes the control flow for subtle bypasses. Moreover, the integration of role‑based libraries from OpenZeppelin affords a declarative syntax that mitigates human error, yet it is not a panacea; incorrect configuration of roles can introduce its own vulnerabilities. Therefore, a balanced approach-leveraging both static analysis and manual code walk‑throughs-offers the most robust defense. In practice, developers should write unit tests that simulate unauthorized calls, ensuring that require statements fire as intended. Pair these tests with a formal specification of invariant properties, perhaps using tools like Certora or the K Framework, to achieve provable guarantees. Finally, remember that security is a process, not a product; regular audits, community reviews, and timely patches are essential to maintain resilience over time.
Emma, your upbeat tone really brightens the discussion! Just a gentle reminder: while colorful language engages readers, always pair it with concrete code snippets so newcomers can see the exact implementation of AccessControl and timelocks.
Nice point.
Oh, the drama of ignoring OpenZeppelin! One might think it’s a trivial oversight, yet it invites the specter of chaos, turning a promising project into a cautionary tale worthy of theatrical lament.
While Edgardo’s thorough enumeration is commendable, let us not forget that an over‑reliance on formal methods can alienate developers lacking academic training; a balanced framework that includes pragmatic testing is paramount.
Man, you sound like a professor lecturing about formal proofs. Sometimes a simple sanity check in Remix can catch the same bug without all the heavy math.
Great insight! 👍 Keep it up!
Exactly.